BeTNA – BeBroadband® Trust Network Access
![]() Trust Network Access (BeTNA) represents a security paradigm that considers every entity attempting to connect to a network as potentially hostile. Based on ZTNA technology, within the BeTNA framework, a user’s role and permissions become irrelevant. To access internal applications or resources, users must authenticate and continually validate their identity. This is typically achieved through stringent access controls and through ongoing contextual and behavioral verification.
Trust Network Access (BeTNA) represents a security paradigm that considers every entity attempting to connect to a network as potentially hostile. Based on ZTNA technology, within the BeTNA framework, a user’s role and permissions become irrelevant. To access internal applications or resources, users must authenticate and continually validate their identity. This is typically achieved through stringent access controls and through ongoing contextual and behavioral verification.
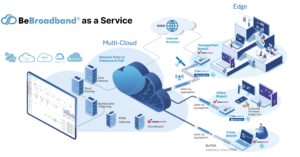
BeTNA has emerged as a crucial response to the challenges posed by highly distributed networks and supply chains. In an era of expanding ecosystems, maintaining direct control over every device and endpoint becomes impractical. Granting unrestricted access to remote users under these circumstances exposes networks to various threats and threat actors.
Here’s a condensed overview of the benefits offered by “BeTNA” (![]() Trust Network Access), a pivotal element within the “BeBroadband® as a Service” platform:
Trust Network Access), a pivotal element within the “BeBroadband® as a Service” platform:
- Enhanced Security:
- Ensures continuous user and device authentication and authorization, mitigating the risk of unauthorized access and lateral movement within the network.
- Integrates security services directly into the network, fortifying the security posture against threats at the network edge.
- Establishes micro-segmented perimeters, strategically limiting the attack surface and posing challenges for lateral movement by potential attackers.
- Improved User Experience:
- Facilitates seamless and secure access from any location, guaranteeing a consistent user experience.
- Optimizes network performance at the edge, reducing latency and enhancing the overall user experience.
- Implements micro-segmentation, allowing users access only to specific resources, thereby improving efficiency and the speed of data access.
- Enables a unified view of users across Edge Devices and any computer with BTNA’s software agent through a single Orchestrator GUI (UI/UX).
- Flexibility and Scalability:
- Enables swift adaptation to evolving business needs with scalable and flexible access controls for various users, devices, and applications.
- Integrates seamlessly with SD-WAN or SASE, offering flexibility in deploying security services where needed to adapt to the dynamic nature of modern networks.
- Easily scales to accommodate a growing number of users and devices without compromising security.
- Reduced Network Complexity:
- Simplifies network architecture by prioritizing identity-based access controls, thereby reducing the complexity associated with traditional perimeter-based security models.
- Consolidates security services at the network edge, streamlining overall network architecture for simplicity and ease of management.
- Simplifies network complexity by establishing secure, direct connections between users and resources, eliminating the need for traditional VPNs and complex configurations.
- Provides a consolidated view of users across Edge Devices and any computer with BeTNA’s software agent through a single Orchestrator GUI (UI/UX).
- Centralized Management:
- Centralized management of access policies ensures consistent security controls across the entire network, regardless of user location.
- Centralized management of security services ensures uniform policy enforcement, efficient monitoring, and swift response to security events.
- Empowers administrators with centralized control to manage and enforce access policies from a single point, enhancing visibility and control over network traffic.
- Offers a unified view of users across Edge Devices and any computer with BeTNA’s software agent through a single Orchestrator GUI (UI/UX).
Benefits of BeTNA:
- Enhanced Network Visibility and Security: BeTNA offers improved network visibility, better vulnerability management, and rapid breach detection.
- Malware Prevention: It helps prevent the propagation of malware.
- Cost Savings: Businesses can reduce both capital and operational cybersecurity expenditures.
- Compliance Simplification: BeTNA reduces the scope and cost associated with compliance initiatives.
- Facilitating Collaboration: It enhances interdepartmental collaboration during disruptive events.
- Data Insight and Protection: BeTNA provides insights into data flow across the network and safeguards against data exfiltration.
- Digital Transformation: It serves as a foundation for digital business transformation.
- Performance Enhancement: BeTNA improves network speed, performance, and the end-user experience.
- Scalability and Policy Management: It offers extensive scalability without the need for additional hardware and simplifies policy management.
By providing direct, segmented access to applications and services, BeTNA inherently enhances security by significantly reducing the potential attack surface. This approach also paves the way for transitioning from Endpoint Detection and Response (EDR) to Extended Detection and Response (XDR).
The most significant advantage of BeTNA lies in its benefits for end users. Businesses integrating BeTNA with robust Endpoint Security can ensure that only legitimate users and healthy devices gain access. This enables support for Bring Your Own Device (BYOD) and remote work initiatives without compromising sensitive assets.
BeTNA Features
Businesses embracing BeTNA will enjoy the following capabilities:
- Continuous verification and validation of access privileges for all resources
- Dynamic access policies adjustable based on user behavior
- Real-time visibility across the entire business ecosystem
- Centralized management of all security controls
- Extended Detection and Response (XDR), ideally supported by cybersecurity AI
- Identity and Access Management
- Multi-Factor Authentication (MFA)
- Security auditing and reporting
How BeTNA Works
Traditional network access relies on two principles: “Trust but verify” and “All users and endpoints within the network are trusted by default.” However, these concepts no longer hold true in a landscape shaped by cloud computing and hybrid work. BeTNA replaces the traditional firewall-based perimeter with a dynamic one based on identity and context. It creates a logical access boundary around applications, limiting access to specific named entities through a trusted broker. This approach conceals applications, reducing the attack surface and thwarting lateral movement.
BeTNA is founded on five key principles:
- Continuous monitoring
- Ongoing validation
- Least-privilege access
- Micro-segmentation
- Device and endpoint authorization
Use Cases for BeTNA
BeTNA can be applied to the following high-level use cases:
- Access Control and Authentication: BeTNA serves as an alternative to IP or account-based access controls found in legacy remote access solutions like VPNs. It allows granular access configuration by defining strict rules around access permissions, including preventing connections from unpatched devices, enforcing approved security software usage, differentiating permissions for personal vs. corporate devices, and adapting permissions based on user location.
- Supply Chain Management: BeTNA is ideal for controlling third-party access to corporate applications, assets, and services. It enables administrators to grant permissions and access to contractors, vendors, or supply chain partners strictly as needed and for the required duration.
- Distributed Cybersecurity: Given the distributed nature of modern networks and workplaces, BeTNA empowers businesses to reduce their attack surface while supporting both distributed and hybrid work models. Integrating BeTNA into an endpoint-focused cybersecurity strategy provides holistic control and visibility across the digital ecosystem.
- Work Form Anywhere: Advanced security service that prioritizes user verification and facilitates access to specific applications based on identity and context policies. By eliminating implicit trust, BeTNA ensures robust control over network movement, reducing potential attack surfaces. Seamlessly integrated into the
 platform, BeTNA offers comprehensive business protection and supports Work From Anywhere (WFA) initiatives, including from the home office. Experience heightened security and flexibility with
platform, BeTNA offers comprehensive business protection and supports Work From Anywhere (WFA) initiatives, including from the home office. Experience heightened security and flexibility with  Trust Network Access.
Trust Network Access.
BeTNA vs. VPN
BeTNA is a modern alternative to VPN technology, which was developed for a different era when businesses had clear security boundaries and stable environments. VPN technology has many limitations that make it less suitable for today’s dynamic and complex ecosystems. Some of these limitations are:
- Security: A VPN gives a remote user access to the whole business network instead of a specific and well-defined segment.
- Performance: VPN connectivity is often slow, inefficient, and complicated due to high resource consumption, clunky interfaces, and long delays.
- Ease of configuration: VPN software is rigid and inflexible, making it hard to adjust security policies and controls based on the situation.
Sharing is caring

