BeBroadband® as a Service Advanced Security
![]() features CloudGuard from Check Point delivers comprehensive security tailored to protect hypervisor-based virtual networks so you can feel confident about extending applications and workflows to cloud enabled environments. This specification document outlines the capabilities of the Advanced Security capabilities which ensures robust security for the device and its associated functions.
features CloudGuard from Check Point delivers comprehensive security tailored to protect hypervisor-based virtual networks so you can feel confident about extending applications and workflows to cloud enabled environments. This specification document outlines the capabilities of the Advanced Security capabilities which ensures robust security for the device and its associated functions.

CloudGuard Network Security gateway The CloudGuard gateway is a security gateway running inside a virtual machine (VM). It provides industry-leading advanced threat prevention security and is deployed into the virtualized network to provide perimeter protection and prevent lateral threat movement between applications inside the datacenter.
Fully integrated security protections
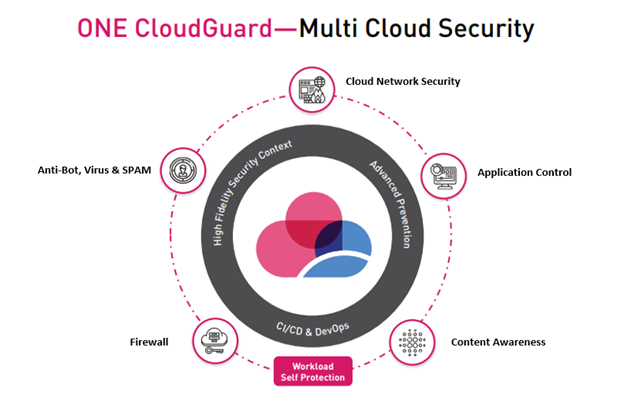
CloudGuard VE provides industry-leading threat prevention security to keep virtualized cloud networks safe from even the most sophisticated attacks. Fully integrated security protections include:
- Firewall, Intrusion Prevention System (IPS), Anti-Virus, and Anti-Bot technology protects services in the cloud from unauthorized access and prevents attacks
- Application Control helps to prevent application-layer Denial of Service (DoS) attacks and protect hybrid cloud services
- Mobile Access allows mobile users to connect to hybrid clouds using an SSL encrypted connection with two-factor authentication and device pairing
- Data Loss Prevention protects sensitive data from theft or unintentional loss
Management of physical and virtual infrastructures
With all aspects of security management such as policy management, logging, monitoring, event analysis and reporting centralized via a single dashboard, security administrators get a holistic view of their security posture across the entire organization. You get complete threat visibility and consistent enforcement for virtual cloud infrastructures. Policy management is simplified with centralized configuration and monitoring of both physical and cloud-based networks, allowing for a consistent security footprint for all corporate data. A layered approach to policy management allows administrators to segment a single policy into sub-policies for customized protections and delegation of duties per application or segment. This ensures that the right level of protection is applied across both physical and cloud networks.
Consolidated logs and reporting
Check Point SmartEvent, part of the Unified Security Management platform, consolidates monitoring, logging and reporting across virtual and physical networks. Virtualized cloud workload traffic is also logged and can be easily viewed within the same dashboard as other logs. Security reports specific to virtualized workloads can be generated to track security compliance across cloud-based infrastructures, dramatically simplifying compliance reporting and audits.
Dynamic security policies
CloudGuard can be configured for integration with a controller component as part of the Security Management platform. The CloudGuard controller integrates with cloud management solutions to include the sharing of context, allowing cloud objects to be imported and reused within Check Point security policies. This reduces security policy creation time from minutes to seconds. Real-time context sharing of cloud objects is maintained so that any changes or new additions are automatically tracked without the need for administrator intervention. Check Point logs are further enriched with cloud context including cloud object names. For example, in a VMware environment, vCenter objects like virtual machine identities and network elements are available in security policies and are populated in logs and reports.
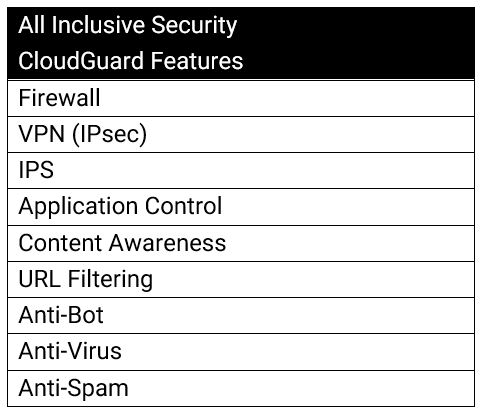
Key features and benefits include:
- Protect the most demanding and business critical virtualized environments using Check Point’s advanced threat protection with highest malware catch rates
- Comprehensive security protections fully integrated into a single security gateway
- Optimally deployed in virtual data centers, branch offices and multi-tenant environments
- Security management for control and visibility across virtual and physical networks
- Shared security context to enable better alignment across security controls
- Seamless integration into private cloud environments for advanced and automated security deployments
Sharing is caring

