BeBroadband® as a Service Application Awareness Security with Deep Packet Inspection (DPI) Security
![]() Application Awareness Security is enabled by Rohde & Schwarz R&S®PACE 2 engine DPI allows. The DPI engine gives visibility and allows blocking and filtering intelligently non-essential applications.
Application Awareness Security is enabled by Rohde & Schwarz R&S®PACE 2 engine DPI allows. The DPI engine gives visibility and allows blocking and filtering intelligently non-essential applications.

Rohde & Schwarz R&S®PACE 2 engine DPI enables ![]() WAN Optimization and next generation advanced security features including:
WAN Optimization and next generation advanced security features including:
- Real-time network protection through next-generation firewalls (NGFW). To effectively address the evolving landscape of cyber threats, encompassing targeted attacks, ransomware, advanced persistent threats, and more, firewalls must employ sophisticated technologies for precise and real-time network protection. With the substantial growth of web-based applications, modern network security devices must not only comprehend network structures but also be proficient in deciphering the language of applications, becoming “application-aware.” The utilization of advanced deep packet inspection (DPI) technology for identifying applications, their services, or application families empowers firewalls to operate intelligently, offering granular visibility and real-time analytics to ensure top level security. By integrating DPI, you can expand the functionalities of your traditional firewall, providing clients with next-generation firewalls that encompass additional layers of the OSI model.
- Benefit from intelligent routing and advanced application security with future-proof deep packet inspection software. Our high-performance DPI engine, R&S®PACE 2, reliably and accurately identifies and classifies thousands of applications and network protocols while extracting valuable metadata in real-time. Unlike previous perimeter security solutions that primarily focused on packet header information, the integration of R&S®PACE 2 into network security solutions allows for in-depth analysis using various classification methodologies, including machine learning and deep learning, leading to reliable and precise IP traffic classification. R&S®PACE 2’s metadata extraction provides insights into crucial attributes such as the host, location, certificates, and version type. Furthermore, by collecting metrics like packet size, packet timing, jitter, latency, and throughput, the DPI engine yields an abundance of network data essential for detecting threats, such as malicious content, application-specific anomalies, and general trends, eliminating blind spots in traffic inspection that are prevalent in today’s networks. The flexibility, scalability, and ease of integration of the DPI engine make it exceptionally well-suited for contemporary distributed networks.
- In zero trust network access (ZTNA) and firewalls, application layer classification is used to identify and control access to applications based on their characteristics, such as their protocol, payload, and destination. This is necessary because traditional network security controls, such as port-based firewalls, are no longer effective in protecting against modern threats.
ZTNA and firewalls can use a variety of techniques to classify applications at the layer 7 level, including:
- Signature-based classification: This technique uses a database of known application signatures to identify applications. The signature database can include information such as the application’s protocol, payload, and destination.
- Heuristic-based classification: This technique uses machine learning algorithms to identify applications based on their behavior. Heuristic-based classification can be used to identify new and unknown applications.
- Deep packet inspection (DPI): This technique inspects the contents of packets to identify applications. DPI can be used to identify applications that are obfuscated or encrypted.
Once applications have been classified, ZTNA and firewalls can use this information to make decisions about access. For example, a ZTNA solution can deny access to an application that is known to be malicious or that is not authorized for the user. A firewall can block traffic to an application that is not allowed on the network.
Application layer classification is a critical component of ZTNA and firewalls. It allows organizations to protect their networks from modern threats and to control access to applications.
Here are some of the benefits of using application layer classification in ZTNA and firewalls:
- Improved security: Application layer classification can help to improve security by blocking access to malicious applications and by controlling access to authorized applications.
- Reduced risk: Application layer classification can help to reduce the risk of data breaches and other security incidents.
- Improved performance: Application layer classification can help to improve performance by optimizing traffic flow and by reducing latency.
- Increased visibility: Application layer classification can help to increase visibility into network traffic and application usage.
Overall, application layer classification is a valuable tool for improving security, reducing risk, improving performance, and increasing visibility in ZTNA and firewalls.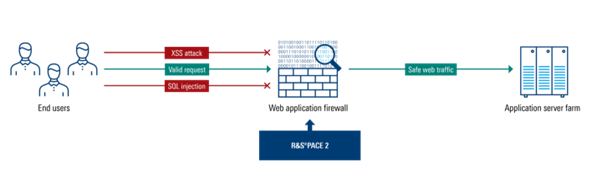
A DPI-enabled firewall capability with application visibility enables:
- Precise application control to thwart threats such as malicious file transfers.
- Detection of obfuscated connections, such as DNS tunneling or P2P-file-sharing.
- Analysis of anonymization protocols like TOR or well-known VPN clients.
- Profile-based anomaly detection, facilitating the identification of suspicious protocol usage in user profiles to prevent data breaches.
- Deception-based security measures to add an additional layer of protection and thwart attackers.
- Fine-grained network access control (NAC) to minimize access from and to the internet and internal network resources.
R&S®PACE 2 offers the following features and capabilities for next-generation firewalls:
- High flexibility and scalability to accommodate diverse customer system requirements.
- The most accurate classification available, enabling efficient network traffic management, encrypted application detection, and optimal network performance.
- Weekly protocol and application signature updates to ensure ongoing accuracy.
- The smallest processing footprint with the most efficient memory and CPU integration in the industry.
Benefits of advanced DPI for firewalls include:
- Efficient management of large network traffic volumes.
- In-depth insights into applications and network traffic.
- Rapid and accurate identification of applications and protocols.
- Comprehensive coverage for VPN protocol classification.
- Preservation of bandwidth and acceleration of business-critical applications to ensure uninterrupted operations.
- Reduction of costs associated with in-house DPI development, implementation, QA testing, and maintenance.
- Assurance of real-time security and policy control.
Sharing is caring

