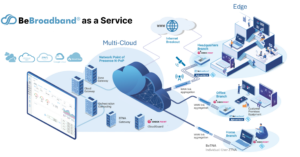
BeBroadband® as a Service Internet Breakout
![]() offers internet breakout where an application may be directed outside of the traditional routing through the BBT.live cloud. Breakout functionality is one element of the extensive feature set that provide customers with secure and highly efficient internet access, prioritizing both performance and security.
offers internet breakout where an application may be directed outside of the traditional routing through the BBT.live cloud. Breakout functionality is one element of the extensive feature set that provide customers with secure and highly efficient internet access, prioritizing both performance and security.
Underlying Features
We will explore the two different types of breakout offered within BeBroadband® as a Service, but first it is important to outline the underlying features that serve as building blocks enabling and supporting secured breakout functionalities.
- Multi-Access Technologies:
- BBeBroadband® as a Service offers support for a diverse range of access technologies, encompassing traditional broadband as well as cutting-edge 4G/5G connections. This adaptability empowers customers to make use of a variety of network options, ensuring a dependable and high-performance internet experience.
- Security Features:
- BeBroadband® as a Service is fortified with a robust suite of security features designed to safeguard customer data and network traffic. These measures include appliance device protection, Next-Generation Firewalls (NGFW), and Zero Trust Network Access (ZTNA). These components collaborate seamlessly to shield against cyber threats and unauthorized access from the edge to the cloud.
- Overlay and Tunnels:
- BeBroadband® as a Service architecture leverages overlay networks and tunnels to oversee and optimize traffic routing. Overlay networks enable the creation of virtual networks that coexist harmoniously with the physical network infrastructure. Tunnels are instrumental in establishing secure communication pathways between distinct network points, including edge devices and the BeBroadband® cloud.
- Traffic Steering:
- Breakout architecture is engineered for the efficient routing of network traffic. Layer 7 (L7) traffic, encompassing specific applications and protocols, can be directed to the underlying infrastructure outside the BBT.live cloud. This allows certain types of traffic to bypass the cloud, utilizing alternate routes for enhanced performance, but continue to maintain the choice of the best performing links and tunnels per application.
- Security Control and Monitoring:
- Traffic and network applications routed to the overlay or tunnels undergo rigorous security control and monitoring. This ensures that data remains safeguarded and adheres to security policies. The tunnels are secured with AES-256 encryption ensuring that sensitive data and applications are shielded from potential threats.
BeBroadband® as a Service Internet Breakout
BeBroadband® as a Service breakout features two options Cloud Breakout and Local Breakout. The choice between Cloud Breakout and Local Breakout depends on the specific security and access preferences of the customer, as well as their existing network architecture. Each option offers its own set of advantages and considerations, allowing customers to tailor their internet access approach to their unique requirements.
WAN optimization, based on Deep Packet Inspection (DPI), plays a crucial role in enhancing the performance and efficiency of both breakout options:
Breakout Options:
The key distinction between the options lies in how internet traffic is routed:
- Cloud Breakout:
- Internet traffic from users is directed through the BBT.live cloud infrastructure before accessing external resources on the internet. This route is typically chosen for its centralized security (e.g., NG-FW) and monitoring capabilities, allowing BBT.live to apply its security features and policies to the traffic passing through the cloud and out to the internet.
- With DPI-driven WAN optimization in Cloud Breakout, BBT.live can intelligently analyze and prioritize data packets at a granular level. This allows for the identification and prioritization of critical applications and services. By understanding the nature of the data being transmitted, BBT.live can apply optimization techniques to ensure that essential applications receive sufficient bandwidth and resources over relevant overlay secured tunnels. This leads to improved performance and responsiveness, particularly for delay-sensitive applications.
- Local Breakout:
- Conversely, with Local Breakout, internet traffic from users bypasses the BBT.live cloud infrastructure and directly accesses external resources on the internet. In this scenario, security and monitoring are primarily dependent on the customer’s network and device security features. This option may be considered when customers have their own security measures in place or prefer a more direct internet access approach.
-
- In the case of Local Breakout, DPI-based WAN optimization continues to be invaluable. By inspecting data packets, BBT.live can optimize traffic directly at the underlay, ensuring that essential applications , even those that don’t require security inspection, receive the necessary resources for efficient transmission. This approach helps streamline data flows and reduces potential latency.
With either breakout option, DPI-based WAN optimization contributes to the overall improvement of network performance, ensuring that applications run smoothly and efficiently. By leveraging DPI technology, BBT.live can fine-tune the handling of data packets, resulting in enhanced user experience and optimized network resource utilization.
Sharing is caring